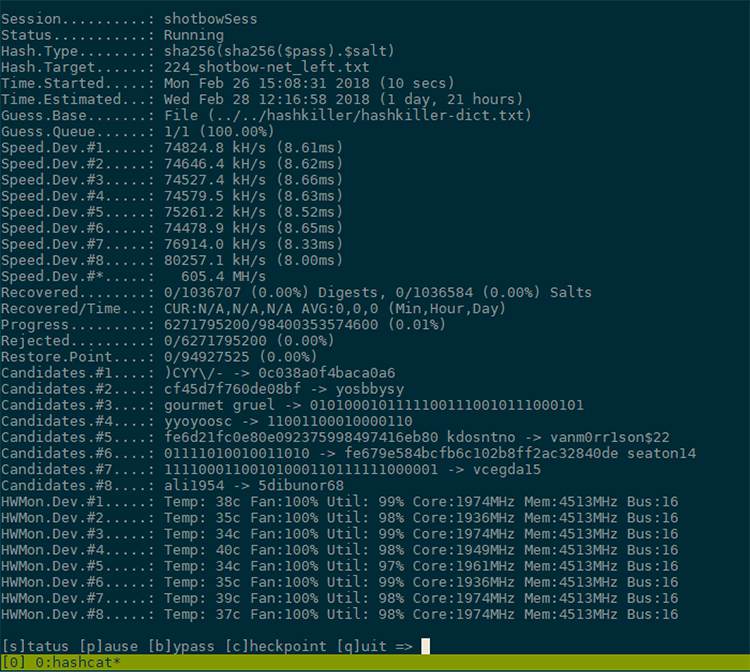
BleepingComputer on Twitter: "Once a threat actor gains access to the NTLM hash, it's as simple as running it through Hashcat to dehash the password. Now the threat actor has both the

Chesapeake Chaos: Join Jerry McNeal And His Ghostly K-9 Partner As They Put Their "Gifts" To Good Use.: 10 : Burton, Sherry A.: Amazon.com.be: Books

Killer Shrimp Restaurant & Bar on Instagram: “Nothing beats a piping hot Traditional Eggs Benedict for breakfast! Served with a side of hash browns, home fries, or fruit. Make sure to…”
GitHub - shauryasharma-05/PortableKanBan-Hash-Killer: PortableKanBan stores credentials in an encrypted format.

![Hashkiller - Kali Linux - An Ethical Hacker's Cookbook [Book] Hashkiller - Kali Linux - An Ethical Hacker's Cookbook [Book]](https://www.oreilly.com/api/v2/epubs/9781787121829/files/assets/7a0893f5-8a61-4c69-9be4-c06c4d78fe7d.png)












![Hashkiller - Kali Linux - An Ethical Hacker's Cookbook [Book] Hashkiller - Kali Linux - An Ethical Hacker's Cookbook [Book]](https://www.oreilly.com/api/v2/epubs/9781787121829/files/assets/714fa5ac-a3a0-4378-b325-97dee1e71141.png)